Jan's Computer Basics:
Hands On: Networked
 Do you
work with a networked computer? Even in small
companies with just a few computers, the
computers are likely to be networked. Homes with only two computers can
benefit from being networked! If you are taking a course using this web
site, you may be working in a computer lab. Almost certainly the computers in the lab
are networked.
Do you
work with a networked computer? Even in small
companies with just a few computers, the
computers are likely to be networked. Homes with only two computers can
benefit from being networked! If you are taking a course using this web
site, you may be working in a computer lab. Almost certainly the computers in the lab
are networked.
So what is different about computers that are networked?
[The following points come from the questions and experiences of my students with a school network and my own experiences with a home wireless network. Your own network may be quite different. You will need to get the specifics from your network administrator or instructor.]
One of the big benefits of networking computers is the ability to share resources.
Share hardware: A whole lab of student computers can be connected to a single fast laser printer. Fewer printers to buy saves money. The printer does need to be very fast, however, to keep wait times down.
Share software:
A single copy of a program can be installed on the network's server and still be run by all 20 computers at the same time. While a license must
usually be bought for each computer, it is easier to maintain the computers when most things are on the server instead of trying to install and maintain software on all 20! This saves a lot of time, and time is money!
Share files: You can use a computer on the network to store files that several people need to access or to share music or photos easily over the network. No need to copy a file to a flash drive and walk it to another computer or to email it to the person across the hall. Just navigate to the shared space and open the file.
Share Internet connection: A common benefit for a network is sharing an Internet connection with
several computers or devices. A wireless network will even let your smart phone
or tablet connect to the Internet.
So this explains why a set of computers might be networked. But what does it mean to you, the user, to share hardware and software with others?
Logon
 When you first access a network, you will probably have to logon or login (pronounced like two words - "log on"
or "log in"). This means a dialog box will popup and you'll have to type in your ID or user name and a password. The network administrator will have a list of names and passwords and will decide what permissions you will have on the network. You may be restricted to using only certain programs or even just certain files. You might not have permission to even change the color scheme or the screen background. (Some administrators are very suspicious of users!)
When you first access a network, you will probably have to logon or login (pronounced like two words - "log on"
or "log in"). This means a dialog box will popup and you'll have to type in your ID or user name and a password. The network administrator will have a list of names and passwords and will decide what permissions you will have on the network. You may be restricted to using only certain programs or even just certain files. You might not have permission to even change the color scheme or the screen background. (Some administrators are very suspicious of users!)
You may be able to set up a User Profile that will be called up from any computer on the network. This allows you to have your favorite color scheme, background picture, icon arrangement, and other user choices whenever you are logged into the network from ANY computer. You may not have this option in a school situation.
In a computer lab that is open to the general student body, you might need to log on only for functions like email or getting lesson materials for your particular class.
Passwords
 People tend to be very lazy about their passwords. Usually the administrator gives you an ID name and password for your first logon. Then you set your own password. Most people use something easy to remember. Unfortunately that makes it easy for someone else to figure out, too. Using variations of your birthday, your mother's maiden name, your Social Security number or driver's license number, and such is a bad idea. Actual words can be guessed easily, too.
People tend to be very lazy about their passwords. Usually the administrator gives you an ID name and password for your first logon. Then you set your own password. Most people use something easy to remember. Unfortunately that makes it easy for someone else to figure out, too. Using variations of your birthday, your mother's maiden name, your Social Security number or driver's license number, and such is a bad idea. Actual words can be guessed easily, too.
![]() Secure
Passwords: The best password that is secure is a long random string of numbers, characters, and letters mixed up. But you do need to figure out a way to remember your password. (Writing it down and keeping it near the computer is the worst idea of all!) So get creative and take something you can remember but alter it in some creative way. Misspelled words work pretty well - the only time a talent for
misspelling is an advantage! There are a number of free or inexpensive password management programs. Get one and use it!
Secure
Passwords: The best password that is secure is a long random string of numbers, characters, and letters mixed up. But you do need to figure out a way to remember your password. (Writing it down and keeping it near the computer is the worst idea of all!) So get creative and take something you can remember but alter it in some creative way. Misspelled words work pretty well - the only time a talent for
misspelling is an advantage! There are a number of free or inexpensive password management programs. Get one and use it!
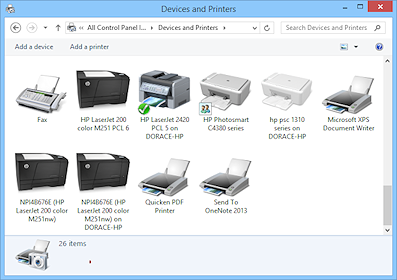
Sharing a Printer
The printer is what you will share most often. On a network, when you ask your program to Print your document, the command goes out to the server that is controlling the printer. Your print job gets in the print queue, that is, it gets in line with other print jobs sent by you or other users on the network and waits its turn.
Depending on your network's setup, a window may popup to tell you when your print job has been sent to the printer and when it has been printed.
View the print queue:
Method 1: Double-click on the printer icon
that displays on the bottom right of the Taskbar when you are printing.
Method 2: Open the list of printers (Start > Printers and Faxes or Devices and Printers) and double-click the icon of the printer you want to view.


Win8, Win8.1 Win10: Open the Control Panel and then Devices and Printers. Right click the icon of the printer and choose 'See what's printing'.
Shared printers have a symbol on the printer's icon, which is different for different versions of Windows. The two examples show a hand outstretched and two identical figures.
The default printer for this computer will have a checkmark of some sort on its icon.
The only print job that you can manage is the one from the computer you are using. This is a good thing! I don't want other folks deleting my print jobs so they can get their documents printed first!!
The window below shows a print queue, the list of documents waiting to be printed. You can see the name of document, the owner (the login of the person or the name of the computer that sent the job to the printer), the size of the document, and the time the job was sent. The Status column shows whether the job is printing now or is paused or has an error.
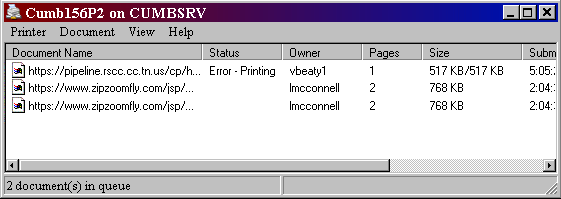
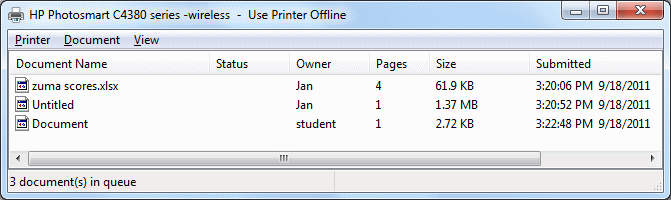
Sent again too fast: In the first example above, it looks like someone got fumble-fingered since jobs 2 and 3 have the same document name and are from the same person and apparently have the same time sent. Probably the popup message did not appear or the printer did not start printing right away. Thinking that the command had not been executed after all, the user clicked that Print button again. Sending jobs quickly like that can give them the same time stamp. You have to wait sometimes for the message to popup that your job has been sent. Be patient!
Printing error: Notice the Error on the first job. It doesn't tell us much. It might mean that something has gone wrong with the printer. Perhaps it is out of paper or the paper has jammed. But it could mean that the server is too busy right this second to handle the print job. So don't panic. Wait a few seconds. The server may get free enough to go ahead with the job shortly. Don't send the job again until you clear the old job out of the print queue. Don't do that until you are SURE that you need to do so.
Notification: Once your print job has been sent, you are free to continue work on whatever tasks you like. You may be notified by a little message or a bell when your pages are actually printed, or maybe not. Your computer thinks the job's finished when the order is sent out to the server. The server would have to send you a message that the actual printing had finished and that requires a printer that talks back to the server. On our little network at school this did not happen. You could watch the jobs vanishing off the queue, but that just meant that the printer's memory had the info now. It didn't mean that the pages were actually printed yet. You had to go look at the printer yourself.
![]() Identify documents: When printing in a shared environment, be sure that your document can be identified as YOURS. You might get busy on another task and leave the printed pages sitting in the printer's Outbox. If you expect anybody else who is using the printer to respect your work (and not trash it!), they need to be able to tell whose it is.
Identify documents: When printing in a shared environment, be sure that your document can be identified as YOURS. You might get busy on another task and leave the printed pages sitting in the printer's Outbox. If you expect anybody else who is using the printer to respect your work (and not trash it!), they need to be able to tell whose it is.
How to identify documents:
- Put your name in the header or footer so it will print on each page.
- Add a new page at the beginning of your document. Include on that cover page your name, the name of the document, and how many pages there are in addition to the cover sheet. This is commonly done for faxes for the same reason - too many documents from too many people or computers in the same Out tray.
![]() Class work: In a classroom setting, it is very important to put your name on the page somewhere, perhaps in the header or footer. Several of your classmates may be working on the same assignment at the same time. Once the pages are in the printer's stack of finished pages, you need to be able to tell whose identical document is whose. (Surely all of you did the assignment correctly. Right??)
Class work: In a classroom setting, it is very important to put your name on the page somewhere, perhaps in the header or footer. Several of your classmates may be working on the same assignment at the same time. Once the pages are in the printer's stack of finished pages, you need to be able to tell whose identical document is whose. (Surely all of you did the assignment correctly. Right??)
![]() Don't delete your document until you have the print-out in your hands! Save it, at least temporarily. If the power goes out or the printer has to be reset
because it is thoroughly confused, your print job may be gone forever. If you don't have a copy of the document
somewhere, you'll have to recreate it from scratch.
Don't delete your document until you have the print-out in your hands! Save it, at least temporarily. If the power goes out or the printer has to be reset
because it is thoroughly confused, your print job may be gone forever. If you don't have a copy of the document
somewhere, you'll have to recreate it from scratch. ![]()
Good Manners
Good manners and good sense tell you not to damage the computer or its contents! This can get you kicked out of the lab, out of the class, out of work.
Crumbs, liquids, kicks, pounding fists can all damage a computer physically. How could you damage the computer's contents? Moving or deleting files and folders, renaming files, changing system file information, formatting hard drives, deliberately infecting the computer with a virus are all ways to get in big trouble.
![]() Clean up after yourself. Don't leave files on a network hard drive unless you have been assigned specific space for saving files. If you need to save something temporarily as you work, be sure to get rid of it before you leave.
Clean up after yourself. Don't leave files on a network hard drive unless you have been assigned specific space for saving files. If you need to save something temporarily as you work, be sure to get rid of it before you leave.
Besides being good manners, you must assume that anything you save to the hard drive might be read by someone else. Also, you cannot be sure that it will be there when you come back. Administrators will clean up the hard drive from time to time, deleting files that are not part of the original installation. If you want to work on a document later, you need to save it to a removable disk and bring it back with you.
Malware: Virus, Trojan, Worm
 There
are far too many nasty electronic critters out there trying to get into your
computer! Malware is a term that covers any kind of
software that has hostile, intrusive, or criminal intent. The most common terms for these
program are virus, Trojan,
and worm. Often the
word 'virus' is used in a way that covers all of these, plus any other
variety of disruptive or destructive attack. Some of the terms for these evil
programs are based on the delivery system and some on the intended effect.
There
are far too many nasty electronic critters out there trying to get into your
computer! Malware is a term that covers any kind of
software that has hostile, intrusive, or criminal intent. The most common terms for these
program are virus, Trojan,
and worm. Often the
word 'virus' is used in a way that covers all of these, plus any other
variety of disruptive or destructive attack. Some of the terms for these evil
programs are based on the delivery system and some on the intended effect.
-
Computer Virus: An unwanted computer program that tries to replicate itself and spread to other computers, often by hiding inside other files or programs. It is often destructive to the infected computer's data and or to the operation of the computer and its programs.
-
Trojan: (short for Trojan horse) A program that does not appear to be destructive but which, in fact, allows others to access your data, to record your logins and passwords, or to destroy or alter your data.
- Worm: An unwanted computer program that duplicates itself across a computer network. It uses up the network's storage space and resources and can interfere with the ability of the network to function at all.
The whole idea behind these nasty creatures is for them to duplicate themselves everywhere possible. Many will quickly copy themselves onto all the hard disks and all the removable disks that are used with any infected computer. They may use your email program to mail themselves to everyone in your address book. They may install a key-logger to track your keystrokes as you enter password and logon info for your bank account.
Once infected, a network can be haunted by any of these types of malware. To completely disinfect the network requires disinfecting every disk and every file!
Prevention of infection is much better. So most networks run some kind of antivirus program regularly. Modern antivirus programs test for more than just plain viruses. They look for all kinds of destructive and annoying programs. You should let such software run in the background while you work. The software can catch a virus/trojan/worm before it has time to spread. Ask your network administrator how to use your network's antivirus program. Then use it!
![]() Check
before opening: Set your software to check every removable disk for viruses,
etc., before it will be accessible to the network. The disk may have picked up a virus long ago and you not
even know it. Some viruses only activate after a certain date or after a certain file is run. So you could have an infected disk for awhile before it tries to do anything nasty. This is the way networks get re-infected after thinking that the battle has been won.
Check
before opening: Set your software to check every removable disk for viruses,
etc., before it will be accessible to the network. The disk may have picked up a virus long ago and you not
even know it. Some viruses only activate after a certain date or after a certain file is run. So you could have an infected disk for awhile before it tries to do anything nasty. This is the way networks get re-infected after thinking that the battle has been won.
Sneak Attacks: Social Engineering
There are many ways evil-doers try to get you to help them in their schemes. Their methods use social engineering to trick you into revealing important information, like your Social Security number or logon information for your bank. They rely on your social connections to friends and family and your trust of the institutions that you work with.
Fake update request: You receive an email that appears to be from a trusted source - your bank or electric company or credit card company. The message provides a link for you to use to "update" your records for some 'logical' reason. It is a lie! The link is not to the regular web site! If you fill out their update form, you are sharing your important, private information with criminals!
Solution: Don't use the links in emails. Go to the site yourself directly and do your updating there. Also, most major sites have a page about current schemes like this and a link for you to use to report new ones.
Cool site scam: You get a message that appears to be from your Mom or a trusted friend but it is not a personal message. It has a link to a "funny" or "cool" website, with little detail about what to expect.
Solution: If it seems off at all, don't go there. Verify with the sender that it actually is a good site. (Your friend is savvy about technology, right?) When you send links to others yourself, make sure you write a personal message that makes it clear that this is not a fake message. Be sure that the site is legitimate! A statement like "This is for real" is not enough!
Fake emergency: You get a message asking you to send money to get a friend or relative out of a jam in a foreign country or far from home which says something like "Please don't tell anyone. I am so embarrassed to be in this fix." When you click on the link or follow the instructions, more happens that you know! Malware can be installed on your computer. Plus, you lose all the money in the bank account that you so kindly told them about.
Solution: Verify that your friend or relative really needs help before sending any money. Don't send it directly from your bank account to an overseas location. If they can email you, why can't they phone??
If you get into trouble far from home, forget the embarrassment part! Call so you can prove who you are. Don't leave home without telling your loved ones where you are going to be. You certainly don't want an actual call for help to be treated as a scam!